When buying a Secure Access Service Edge (SASE) solution, comparing features is the easiest part of a SASE acquisition process. A well-designed table and a bit of vendor honesty (or, more likely, head smashing on your part) will get you the capabilites provided by various SASE vendors.
No, the bigger challenge in selecting a SASE solution is understanding the packaging of those capabilities. As we’ve long seen with Cisco, simply having the capabilites does not make an enterprise solution. How well those capabilites are packaged, integrated together, and delivered is essential.
Such is the challenge with Palo Alto Networks. No doubt that Palo will provide you with a robust security offer. And there’s no question you can get a solid SD-WAN solution from them as well. The big question for anyone considering Palo is the packaging and integration of its many features.
After all, SD-WAN only became a serious offering for Palo Alto last year with the acquisition of CloudGenix. Since then, the company has acquired The Crypsis Group for incident response and Expanse for attack surface management technology all in an effort to becoming a SASE vendor. The range of products introduce complexity, which is anathema to the SASE principle of operational simplicity. What’s more, the lack of a private backbone means the company must rely on the public Internet for site-to-site connectivity. This might not be an issue with small or even regional companies, but should be a warning to any global enterprise.
SASE in Brief
Before we dive into the Palo platform, let’s level-set on what is SASE. Secure Access Service Edge (SASE) was introduced by Gartner in 2019 largely in response to the cost and complexity of legacy enterprise networks. There are the high cost and headaches of legacy carrier MPLS services, which are well known. There is also the sheer number of appliances and point solutions that define the enterprise network. With so many solutions, troubleshooting has become incredibly complicated, and network operations are challenging at best. Finally, security is particularly challenging for many companies, requiring so many individual security appliances and products to be deployed, integrated, maintained, and patched to stay current with the latest threats. It was a burden well known to anyone who has worked in the area.
Gartner understood all these challenges and defined SASE to address them. SASE is as an architecture that converges the functions of network and security point solutions into a unified, global cloud-native service. It’s one global cloud service, connecting all enterprise edges— sites, remote users, public cloud applications, cloud data centers, and IoT devices — protecting them with one set of security services — NGFW, IPS, SWG, CASB, anti-malware, and a host of others.
It’s this convergence of networking and security, backbone, and cloud that makes SASE unique. Features and functions of SASE are not new or at least shouldn’t be. But converging them all together into a unified, cloud-native global service is very new and enables IT organizations to become more efficient and agile.
Prisma Access: Palo Alto’s SASE Service
So that’s SASE, and the Prisma Access SASE service is Palo’s SASE solution. How does it compare with the SASE defined by Gartner? Let’s take a look.
Prisma Access is comprised of two service layers: networking and security. The networking layer is supported by various components. High-capacity CloudGenix SD-WAN appliances (recently renamed Prisma SD-WAN) are available for the on-prem datacenter; virtual equivalents for cloud datacenters. Smaller models of the appliances go in branch or retail locations. The data center locations are protected by integrated Palo Alto NextGen firewalls; branch office and retail locations are supported by Palo Alto’s Firewall as a Service (FWaaS).
There are VPN options, including IPsec, SSL/IPsec, and clientless VPN for connecting users and networks. Prisma Access Zero Trust network access (ZTNA) can also provide access for remote users to data centers or applications they need.
The security layer of Prisma Access SASE is Palo Alto’s sweet spot. In addition to the FWaaS mentioned earlier, the security layer includes:
- DNS security to protect against threats in DNS traffic,
- threat prevention to block exploits, malware and command-and-control traffic,
- cloud secure web gateway (SWG) to block malicious websites,
- data loss prevention (DLP) that categorizes sensitive data and applies policies to control access, and
- cloud access security broker (CASB), which adds governance and data classification to stop threats.
Prisma Access requires a subscription to Cortex Data Lake to store network logs generated and used by the security products.
Prisma Access supports two management options. Panorama network security management is recommended for centralized administration across Palo Alto Networks NextGen firewalls and Prisma Access. A second option eschews Panorama and uses a less feature-rich application in Prisma Access.
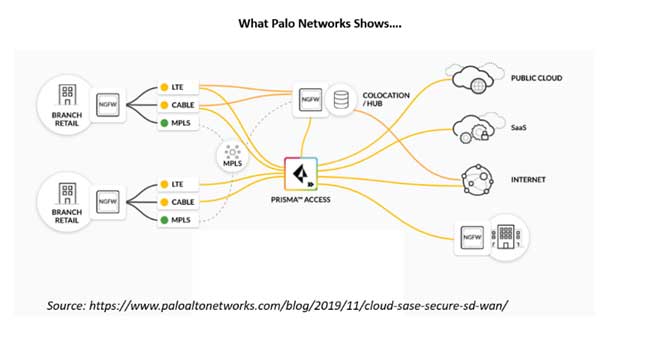
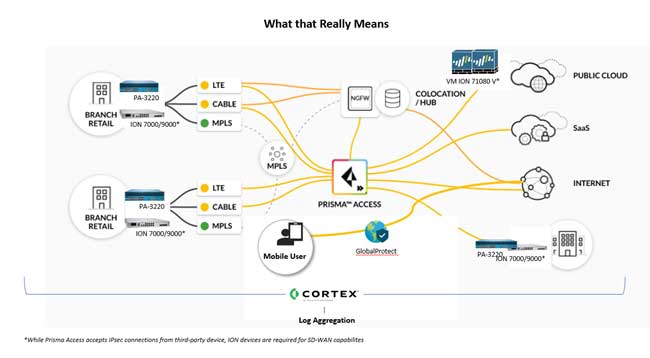
Prisma Access SASE Solution Strengths
Palo Alto Networks views the world of enterprise networking through the prism of strong security, and the company’s SASE offering is no different. Traffic is scrutinized through several security layers to ensure it is free of threats. Palo Alto brings its industry leadership in security intelligence to bear here.
To bolster the networking side, the company spent a year integrating the CloudGenix SD-WAN and the cloud security product, Prisma Access. At the same time, the Palo Alto platform is open; a third-party SD-WAN can be used in place of CloudGenix, or an alternate third-party cloud security stack can be used to anchor security for the CloudGenix SD-WAN. This extensibility allows customers to use whatever products they already have, rather than ripping and replacing existing technologies.
Prisma Access SASE Solution Weaknesses
This SASE solution has various weaknesses, primarily stemming from the fact that it is not a multi-tenant architecture that you would see with a true cloud service. Palo Alto uses virtual instances of their VM-Series firewalls for security enforcement. Traffic routing and processing occurs primarily in the SD-WAN edge device, not the cloud. The only part of that process that’s cloud-native is arguably the least important part — the orchestration layer that spins up and down the virtual instance.
Nor are the security and networking planes of the SASE solution “converged,” despite the company’s claims as such. Rather, they are integrated legacy solutions that still function in separate planes. Traffic passing through those planes must be inspected for routing and security purposes in a daisy-chain fashion, which adds latency as traffic passes through each function.
In its 2019 strategic roadmap for networking report, Gartner wrote that “future network innovation will target operational simplicity.” Palo Alto’s solution is anything but simple because it is largely built around appliances implemented in the edge locations.
Complex Configurations Are Hard to Manage
To achieve SD-WAN connectivity, customers must deploy CloudGenix ION appliances in on-prem and cloud data centers and at the branches. These appliances have a basic built-in firewall, but if that isn’t sufficient (which is 99% of the cases), customers must also deploy a Palo Alto NextGen firewall in these edge locations. The two types of firewalls require different management solutions—Prisma SD-WAN and Panorama. If the customer requires a high availability solution, the appliances must be duplicated at each site. Complexity grows with each customer requirement. Worse, it is not flexible and future-proof—unable to change and grow with the customer’s needs.
No Private Backbone. Third-Party Clouds Host the PoPs
Palo Alto lacks a private backbone, instead building its PoPs on third-party cloud platforms, namely Google’s GCP and Amazon AWS. This is in direct conflict with Gartner’s recommendation that SASE providers shouldn’t build their offering on someone else’s cloud. Failing to own the underlying cloud infrastructure limits their control over the routing and their ability to expand to match the geographic requirements of their users. It also means that expecting to replace a predictable, global MPLS network with Palo Alto is not likely to happen.
What’s more, Palo Alto’s marketing materials claim 100+ PoPs in 75+ countries, but that’s misleading. A PoP for Palo Alto is a point where customers connect their edge sites to the SASE provider, but the processing of that traffic occurs in a separate compute location. Your traffic must first be backhauled to that location, which adds latency, impacting performance. Today, GCP only has 24 compute locations (called regions) in the world.
A real-life scenario: traffic that originates in Peru. Palo Alto has a PoP in Peru for network connectivity, but the nearest GCP compute center is in Brazil. So, traffic originating in Peru must be first forwarded to Brazil —a 200 millisecond round trip time away. This makes the added latency untenable for many applications.
Optimization Is Limited
Palo Alto claims to offer optimization for SaaS applications, but this claim only covers a handful of applications where peering is available in GCP. Again, this adds latency to many cloud-hosted applications which makes for a poor user experience.
Palo Alto’s SASE Solution Is a Square Peg in a Round Hole
Palo Alto’s Prisma Access SASE solution looks good on paper. It comes from a company with a strong pedigree in security with components rich in features. But precisely because these products were built as stand-alone solutions, you should carefully consider if Palo’s SASE solution is a good fit. The lack of tight integration between the components makes deployment challenging. Failure to deliver a true cloud service further complicates deployment and means you can expect to continue with all of the challenges endemic to appliances. And, finally, the lack of a private backbone strongly suggests that performance will suffer, particularly in global deployments.



